NcryptNshare
Secure File SharingNcryptNshare
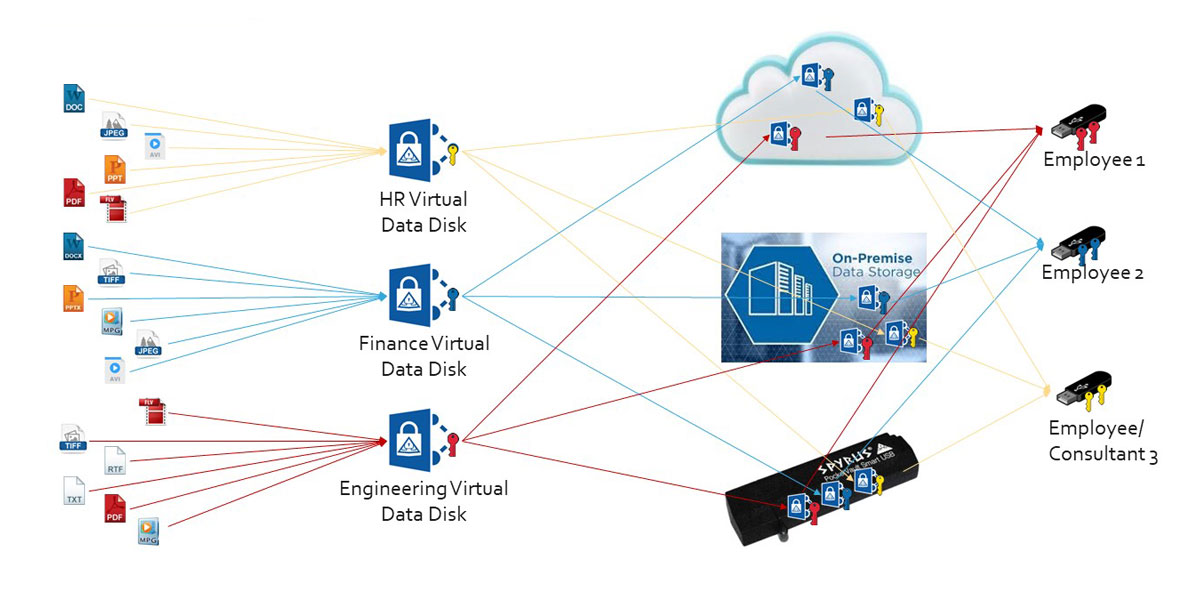
NcryptNshare provides the highest level of object encryption and controlled access so that cloud or other unsecured communication locations/paths can be used with complete confidence for the data’s integrity and security.
How NcryptNshare Works

The SPYRUS patented “seal” of the encrypted file prohibits any tampering (for instance by malware), ensuring data is protected wherever it is stored.
SPYRUS also provides data recovery capability that can be managed by the enterprise should a user’s key be lost, disabled or destroyed.
NcryptNshare operates within the SPYRUS Hardware Roots of Trust (known as “Rosetta”). Rosetta is a FIPS 140-2 Level 3 validated security controller chip embedded in all PocketVault P-3X tokens.
In addition to being antitamper, Rosetta offers a comprehensive list of cryptographic functions with RSA, elliptic curve and custom algorithms.
By leveraging the key protection of Rosetta, NcryptNshare allows users to dynamically assign access to encrypted objects to enforces multifactor authentication, ensuring that only the right user(s) have access to the information being shared.
NcryptNshare implements next generation elliptic curve cryptography, an interoperable cryptographic base recommended by NIST and global government organizations for both unclassified and classified information.
Features and Benefits:
- Encrypt and share all file types anywhere with the highest level of confidence.
- Decryption keys are in the hands of the data owner and those data is shared with.
- Patented technology reconstitutes keys as required.
- Defense in Depth Data Protection uses a double layer of encryption to protect data at rest.
- Support sharing with individuals or groups.
- Protected data can be stored in popular cloud collaboration systems to provide military grade data protection while keeping the keys in the hands of the data owners and those they choose to share it with.
- Recovery agent supports continuity for decryption in case the primary Rosetta key is lost or stolen.
- Protected data can be made read-only to prevent modification.
- Cryptographic binding permits read-only virtual vaults to be securely accessed without modification for forensic applications.
- Expiration date allows the sender to control the time duration of exposure to sensitive data.
- Digital signature assures data integrity and the originator’s identity authenticates that the package was created by the publisher.
- KeyWitness Notary Mode option enforces the use of hardware-based digital signature keys, providing file level non-repudiation.
- Rosetta PKI HSM functionality generated key pairs, store digital certificates, digitally sign and encrypt email, and enables strong authentication.
- File permissions can be set to disable printing and saving unencrypted versions of the file.
- Optional on-premise or cloud PocketVault P-3X token management platform for managing PocketVault P-3X tokens.