FEDERAL GOVERNMENT
Securely leveraging data to generate exceptional outcomesIt’s all about data

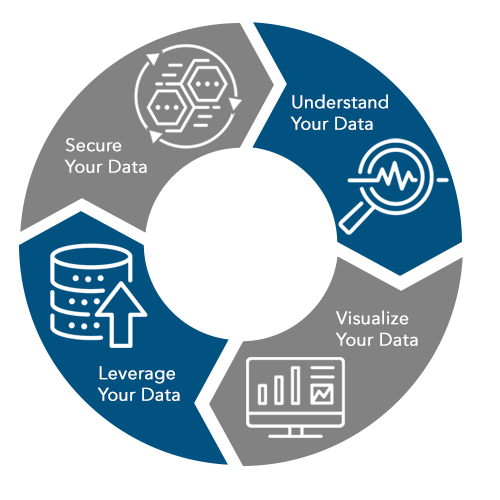
Data, and the information it yields, now constitutes the greatest potential advantage in business, in government, and in military superiority. To capitalize on that advantage, we have to do a better job of securing and accessing our data, analyzing and leveraging it, visualizing it, and putting it into practical use.
Secure and access your data
What incidences like the coronavirus crisis have taught us is the importance of systems that can adapt to unprecedented conditions without interruption. This includes technologies that enable our government and military personnel to change where and when they work while continuing to operate effectively, without adding any new risk.
What the past decade has taught us is that we need to do a better job of keeping data secure. A recent cybersecurity readiness review prepared for the Secretary of the Navy found that “long-term, U.S. future military advantage is being diminished by years of IP exfiltration from the Department of Defense, Department of the Navy, and Defense Industrial Base1.”
Human error accounts for the majority of data security compromise, so we have to stop trusting humans not to err. We also need to secure data without putting constraints on where personnel are located. This involves finding a way for personnel to access data securely, without relying on them to ensure that access remains secure, as well as positively validating the identity of mobile users. Fulfilling both of these needs has proven challenging.
The Safest Solution: Don’t move data
As soon as you move data, there is risk. Virtual private networks (VPNs) are a great example of this. VPN is not a technology that has multi-factor authentication built in, so the validation of user identity is an added risk. Ostensibly secure, VPN functionality requires data and files to leave the network perimeter and travel to less secure computers or devices. If such devices are lost or stolen, you have a potential problem because of the sensitive data they contain.
“As soon as you move data, there is a risk.”
VPNs themselves are also vulnerable in several ways. VPNs are delicate: they can and do collapse under their own weight, as the coronavirus crisis showed us. At that time, multiple federal VPNs were not able to support a massive spike in number of users, and networks crashed. VPNs are also vulnerable: in January 2020, the Department of Homeland Security issued a National Cyber Awareness System Alert2 regarding the vulnerability of over 14,000 VPN servers worldwide—the same vulnerability that allowed hackers to infiltrate and ransom Travelex systems around the world3. For further reading, see What Is a VPN?
Access data in place
The solution is to avoid moving data. Enable personnel to work with it, but leave it in place. Thanks to accredited Route1 solutions, U.S. military personnel and federal workers currently have the ability to access their full desktops while away from the office and outside of the network perimeter, without moving data. We have also provided the United States government and military with the same means that they have in use for physical and logical user validation, when validating the identity of mobile users. It is compliant with United States Department of Defense requirements (Common Access Cards for military personnel and HSPD-12 PIV card mandate for civilian government employees and contractors).
If You Must Move Data: Harden Endpoints
The mission of Government is very broad and involves protecting, providing for its citizens. In the U.S., numerous Federal agencies and commissions manage the country’s space program, protect its borders, and gather intelligence, for example.
In many scenarios, government agents often travel into foreign countries, and must continue to be productive in proximity to well-funded, sophisticated agents of foreign powers. Military equipment and devices must function in environments with unique characteristics—in a Humvee, onboard a fighter jet, remote locations at sea—and must be rugged enough to continue to function, sometimes for years unattended, and maintain data security – whether the data is at rest, in transit or in use.
Access data in motion
True zero-trust, that can’t rely on “data in place” requires a verified security solution that has been proven to be tamper-proof and remotely administered or “killed” from a thoroughly envisioned and tested management solution. Our device management server provides enterprise management capabilities that enable administrators to centrally register, block/unblock, revoke, set polices, integrate third party applications for secured access, audit, and “kill” devices remotely. Additionally, each time the user is connected to the platform, the audit functionality is synchronized, allowing the enterprise to monitor user actions as well as control access to the use of the devices in the ecosystem. By capturing log-on and log-off activity, device disabling and enabling, and activation code recovery actions, government entities can monitor users and devices from structured data that allows the determination of patterns of use and detection of suspect operational behavior, informing corrective action; with the highest level of confidence.
Analyze and Leverage your data
International Data Corporation (IDC) estimates that stored data is growing at a rate of approximately 61% per year4. That’s a lot of data, but most of it goes unused. Harnessing the growing mountains of data we are already collecting, and turning it into valuable information—while keeping it secure and managing access credentials—would allow us to generate exceptional outcomes for our organizations.
Route1 builds data analytics solutions that bring exponential efficiency to manufacturing and other involved processes. They are powered by our patented universal identity management and service delivery platform, MobiNET, guaranteeing military-grade user authentication and security.
When COTS won’t do
There are no commercial, off-the-shelf (COTS) solutions to complicated problems. Whenever we design a solution, be it analytics-based or some other kind of software, it is a custom solution.
When the Joint Service Provider (JSP) amalgamates services and needs to ensure security while delivering ease of accessibility with data in motion, it’s a challenge. That’s where we come in, scoping the project, and using the technologies that we have built within a custom solution to build what they need. The high-level custom software engineering capability that Route1 provides has become very important to the federal government.

Visualize your data
Soldiers used to take orders by field radio. Now it’s rugged smart phones, laptops, tablets and other devices. In the field, laptops and tablets that meet military standards (MIL-STD 810F) are able to withstand the intense heat and sand of the desert, the bumps and jolts of an armored vehicle, and other adverse conditions.
Whether it is military personnel in the field or federal employees in the office, everyone does their job more effectively with the information and communications ability that smart devices can provide. Use of smart devices is a growing trend for other reasons as well. Those devices, while communicating critical information, are capable of gathering useful data on the people they serve: personnel movement, reaction times to electronic alerts, and other metrics that can help improve efficiency.
Procure threat-free equipment
One concern with technology, amply illustrated by the 2019-2020 debate over Huawei 5G implementation in the U.S. and around the world, is its safety from a cybersecurity perspective. A report by the Inspector General of the U.S. Department of Defense found that in 2018 the Army and Air Force Government Purchase Card (GPC) holders bought at least $32.8 million of commercial off-the-shelf (COTS) information technology items with known cybersecurity vulnerabilities.
The report goes on to state that “if the DoD continues to purchase and use COTS information technology items without identifying, assessing, and mitigating the known vulnerabilities associated with COTS information technology items, missions critical to national security could be compromised”5.
Route1 is a provider of military-grade vulnerability-free rugged technology for business, government and our armed forces. Our services include pre-deployment planning, deployment project management and installation, and post-deployment maintenance—a full-service solution. We can also combine this with a tailor-made, device-based analytics program in order to bring further efficiencies to operations.
Install Encryption onto Your Hardware
The proprietary Route1 endpoint management tools provide a hardware-based trust anchor for use in security devices, applications, and processes. It also makes available a comprehensive set of cryptographic capabilities for use in existing, and yet–to–be developed, security applications. Encryption can be disabled to provide full access to the flash memory on the Rosetta microSDHC card, making it available for use as supplemental, removable, and configurable secure memory for use by applications running on the host platform. When encryption is enabled, the trusted flash hardware encryption mode protects access to the flash contents until the user is successfully authenticated to the security controller.

Route1 Authorities to Operate (ATOs)

Security is where Route1 began and continues to excel: we invented data security and user authentication technologies that landed us patents in the U.S. and Canada. We have full ATOs and RMFs with the U.S. Department of Defense including the Pentagon’s Joint Service Provider, the U.S. Army, the U.S. Marine Corps, the U.S. Navy, the U.S. Department of the Interior and other federal government organizations. We have been working with many of these organizations since 2014. Browse U.S. Federal Contract Vehicles
1CyberSecurity Readiness Review prepared for the Secretary of the Navy, March 2019
2CISA Cyber Infrastructure Alert (AA20-010A), January 2020
3Air Travel Cyber-Attacks: New York Airport Hit, Travelex Exchange Held To Ransom, Forbes, January 2020
4Data Age 2025, IDC, April 2019
5Audit of the DoD’s Management of the Cybersecurity Risks for Government Purchase Card Purchases of Commercial Off-the-Shelf Items – Report No. DODIG-2019-106, July 2019